
Recently, I wrote about ft_printf project, you can check my article by clicking.
As we finished our first three projects at Fundamentals Trail, we had the opportunity to create a deep understanding of virtual machines and how this very powerful tool can leverage our technical network knowledge. Debian, shell script, network fundamentals (such as SSH, DHCP, UFW, hostname, ports, etc.), package management (apt, aptitude), user privileges (root, sudo, user), password policy, MariaDb/WordPress configuration, lighttpd server…, crontab, shell script, and a lot of important new concepts.
It is possible to list a large number of new concepts, including services and commands, that we need to understand in order to complete this project. In this post, I am going to describe the most important concepts (in my opinion) within the scope of virtual machines from my perspective as a software engineering student.
If you are looking for a manual or guide to help you in your development, follow this guide.
Disclaimer:
This article represents my perspective about my understanding of the scope of this project, and it might contain incorrect information. If you found any mistakes, I would be grateful if you sent them to me in order to make corrections.
Summary
1. My first experience with virtual machines: Why set up one VM?
2. Linux Debian: The best distribution for servers?
3. Network concepts: SSH, UFW, ports
4. Why and how do you set a strong password policy on your server?
5. CRONTAB!
6. Using Lighttpd, WordPress, MariaDB, and PHP
Virtual Machines and the Power of Virtualization

A virtual machine is a software-based emulation of a physical computer, and you decide what kind of operational system and applications are going
to be used. The hardware available can be used to virtualize virtual machines without interfering with each other. The power of virtual machines lies in their ability to consolidate multiple workloads on a single physical server, improving resource utilization and reducing hardware costs.
Virtualization also enhances flexibility, scalability, and efficiency in managing IT infrastructure. Additionally, VMs facilitate easier backup.
and recovery processes, as well as testing and development environments, contributing to overall system reliability and manageability.
When we compare virtual machines with Docker or container applications, the choice will depend on some variables, as I point out as follows:
Isolation necessity: Docker will use the kernel from the host and isolate only container processes. This fact increases their performance and speed and decreases the hardware requirement. Virtual machines are totally isolated from the host kernel and will need more resources to execute.
Hardware: As we talked about before, virtual machines need more hardware capability, time to execute and run, and resources. It can be a great and powerful tool when we need to test applications whose OS differs from yours or when your changes can ruin the kernel OS of your current machine.
Debian or Rocky?
Debian is free, stable, and a large-community software. It has a large number of adepts (developers, companies, and administrators). Users have the power to choose their tools and applications in order to run their own services as they want. The responsibility is up to him. When we talk about Rocky, it was recently created by Gregory Kurtzer, one of the original creators of CentOS, a RHEL distribution. After Red Hat announced that CentOS would be discontinued, Rocky became a new possibility.
In my Born2Beroot development, I chose to use Debian. It contains more documentation available and, in my opinion, seems to be more stable than Rocky due to its operation since 1993.
In this article you can read more about both distributions.
Network concepts and server security
Being connected online is a big challenge when talking about cybersecurity. With this in mind, we can use a variety of very strong and powerful tools to provide security and make the lives of cybercriminals as hard as possible.
In this context, a UFW firewall is essential because your server will be able to receive connections from the internet only at specified ports. It means that even if your IP address is available, intruders can´t access your server from any port; it would be specified by you, as an admin.
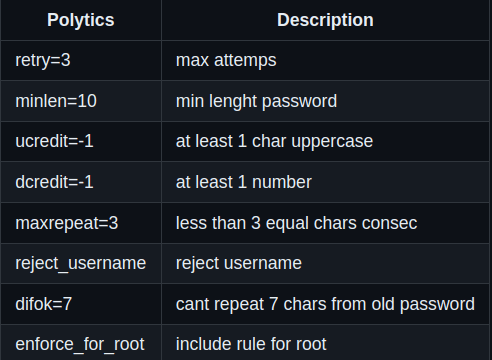
Password policy and why it is crucial to manage it properly
Managing passwords is a hard job. In the perfect scenario, we need to create a unique password for each service or account that we have online. Using software to manage your passwords has been proven dangerous and requires some caution. On your server, as a root (in other words, an unlimited user), you need to be very tough when setting new passwords for yourself, creating good password policies, and not allowing connections via SSH directly to your user (it would be easier for an attacker to use brute force algorithms to crack your account using your IP address).
In the born2beroot scope, we define a strong password policy using the pwquality application and do not allow weak passwords like this:
Sudo users have permission to temporarily elevate their user status to superuser. With this, you have the same privileges as a root on your server.
Crontab and its Power!
How many people are responsible for executing repeated activities excessively daily? Developers can leverage their time and create automated processes from a code perspective.
When using a tool like Crontab, you can give your server the duty of executing steps that you define. In born2beroot, we created a shell script that runs every 10 minutes to show server information, but you can use any kind of script and set any time for repetition that you need. It is an amazing and powerful tool.
Lighttpd, Apache, and Web services
Using a database and setting up a website directly from the server and command line is a new thing for me. But it is not hard as looks like. In the born2beroot bonus part, we set up a new WordPress blog from scratch, being able to access it only within the scope of the school network. We develop an understanding of dynamic and static IP protocols, how to change them and set new IP addresses, create databases like MariaDB, and integrate them all on our server.
Check this article for a deeper understanding in this topic.
Check my github born2beroot repository and fill free to contribute as you want.
One response to “Born2beroot: VM, Debian, And Secure Server Mastery At 42”
[…] It’s been a while since my last article! Last time, I wrote about Virtual Machines. Check my a… […]